The Smartest Way To Make Your People Smarter
Continuous, validated learning that fits conveniently into the workday.

Validate Learning When It Happens
Know your team’s skill levels, reliably, every day. We assess as people learn, continuously, to help you manage talent and learning programs in a whole new way.
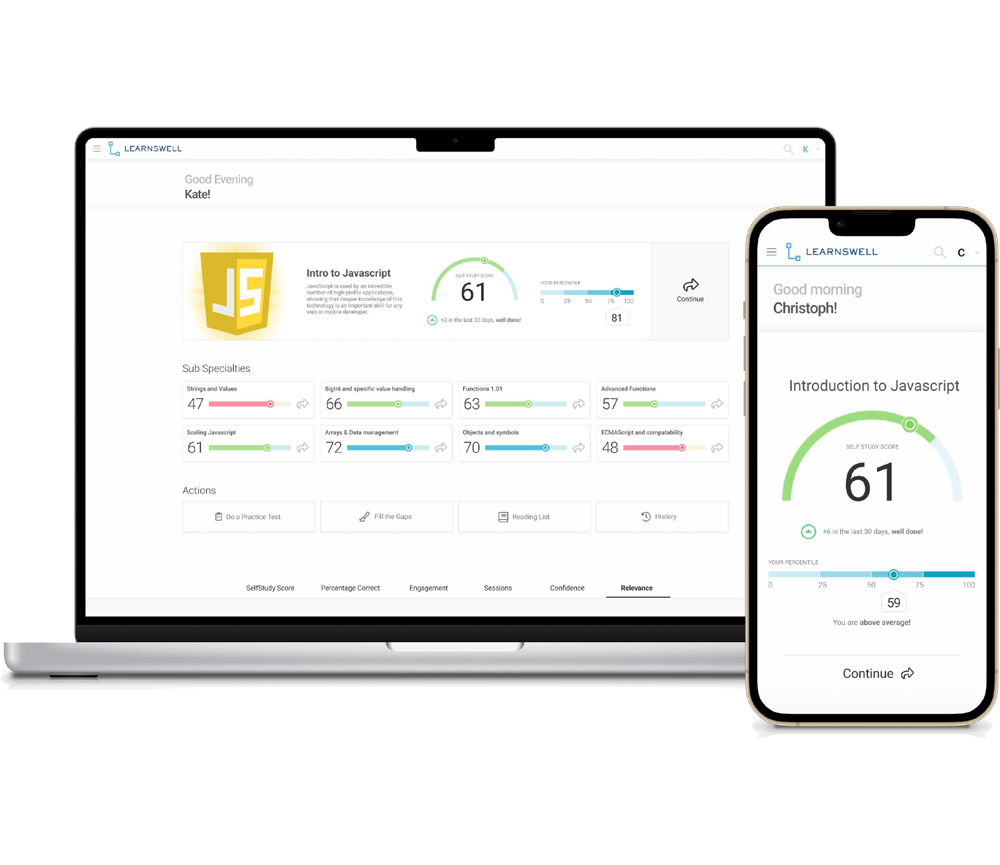
As Easy as Checking Email
Make learning a habit. No need to carve out large blocks of time for classes or seminars. Our patented AI technology delivers a personalized stream of bite-sized lessons, tailored to each learner.
